Network professionals can now receive Stingbox alerts via Syslog. Currently, sending is performed only via the TCP protocol.
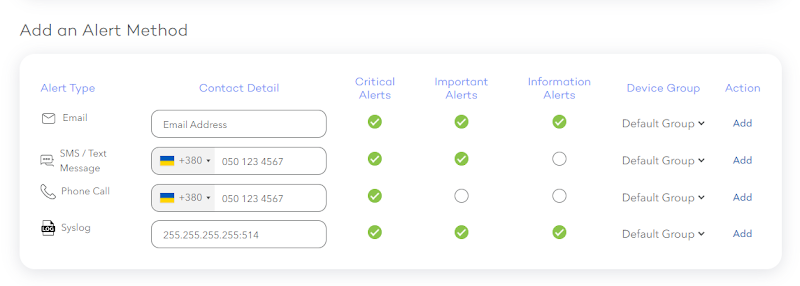
To set up receiving alerts using syslog, you need to configure your server to receive such logs using the TCP protocol. Next, go to the stingbox website and go to the alert methods management page. There you will see this new option at the bottom:
To start receiving syslog alerts, you need to specify here the IP address of your server to which the alerts will be sent, as well as the port used. Follow the format specified in this field: <ip>:<port>
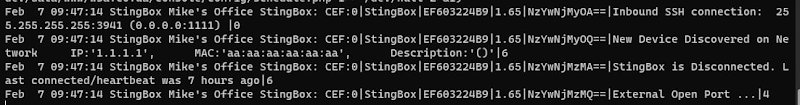
So if you did everything right and entered the correct address, you will receive alerts to this server. Here’s what such notifications look like:
Messages comply with the CEF format. This format implies the following data set:
CEF:Version – CEF version
|Device Vendor – StingBox
|Device Product – the code of your StingBox from which the message was received
|Device Version – your StingBox software version
|Signature ID – unique alert hash
|Name – this is the alert message itself
|Severity – message severity, from 0 (debug) to 7 (emergency)
More information on the CEF format can be found here: CEF WhitePaper